What is WannaCry…?
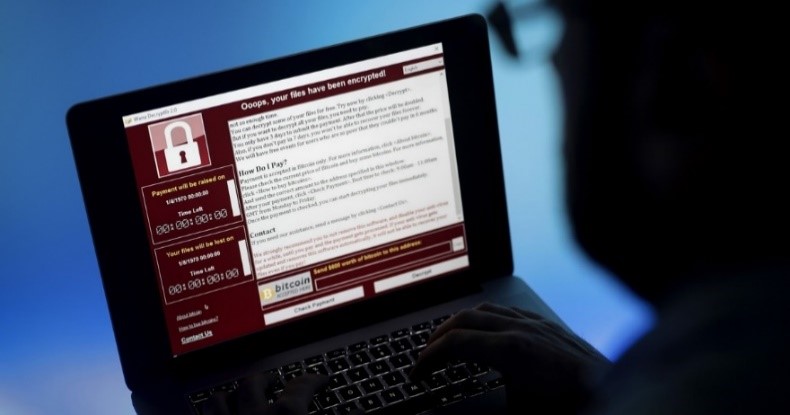
WannaCry is one of the most frequently used buzzwords of 2017. It is a form of cyber-attack. Let’s take a dive into the world of cyber-attacks and find out more about WannaCry. This cyber-attack took place in May 2017 and affected around 230 000 computers in over 150 countries. WannaCry is a ransomware; which is a type of malicious software designed to block access to a computer system until a sum of money is paid. It belongs to the ‘encrypting ransomware’ family. It targeted computers running the outdated versions of Microsoft Windows Operating System (OS) by encrypting data and demanding a ransom payment via Bitcoins. It propagated using the WannaCry worm. It is also known as the ‘Wanna Decryptor’, ‘WCRY’ or as ‘Wanna-Crypt’.
Security experts in Avast and Symantec suspect that WannaCry most likely spread using an exploit used by the Equation Group; a group which allegedly had ties with the NSA (National Security Agency of United States – Department of Defense). It all started after the hacking group that goes by the name ‘Shadow Brokers’, who were able to obtain and started releasing parts of the hacking tools used by the NSA. The vulnerability is linked to Microsoft machines and was found to affect Windows XP, 7, Vista, 8, 8.1, 10 and versions of Windows Server software. This network infection vector, which is called as ‘EternalBlue’, was released by the Shadow Brokers on 8th April 2017. Microsoft Security Bulletin MS17-010 – Critical; is a security update for Microsoft Windows SMB (Server Message Block) Server. This patch for their existing vulnerability in SMB was released on 14th of March, 2017, about 2 months before the WannaCry outbreak. Unfortunately, this patch did not support older Windows XP, Windows Server 2003 and surprisingly Windows 8…!!! (due to the fact that, Windows 8.1 is classified as a mandatory service pack upgrade to Windows 8). To Microsoft’s credit, the day after the WannaCry outbreak, it released security patches for the above retired operating systems too. Subsequent research has indicated that Windows 7 to be the most affected OS out of the lot. ‘Kryptos Logic’ a cyber security firm found that they were unable to infect a Windows XP system with WannaCry using just the exploits. During their attempts, either the payload failed to load, or caused the operating system to crash, rather than actually execute and encrypt files. However, when executed manually, WannaCry could still operate on Windows XP. That could be one of the reasons for the relatively lower number of infected Windows XP running PCs.
How it propagated…?
According to Malwarebytes: “the initial component that gets dropped on systems appears to be a worm that contains and runs the ransomware, spreading itself using the ‘EternalBlue’ SMB vulnerability”. The ‘WinMain’ of this executable first tries to connect to a non-existing website. It doesn’t actually do anything apart from trying to connect. If the connection succeeds, the binary will stop running. Actually, this is sort of a kill switch or an anti-sandbox technique, whichever it is, it backfired on the authors of the worm. (A sandbox is a popular security mechanism for separating running programs. Sandboxes are often used to execute untested or untrusted programs or code.) Security researcher Marcus Hutchins, accidentally discovered the domain name when inspecting the malware’s code and registered it with internet services for a paltry $10.69, thus preventing the spreading of the ransomware. The interesting thing here is, it
had been speculated that this was added to the code as a mechanism to prevent it being run on quarantined machines used by antivirus researchers. He also observed that some sandbox environments will respond to all queries with traffic in order to trick the software into thinking that it is still connected to the Internet, so the software attempts to contact an address which does not exist. Since in a sandbox environment it responds to queries and mimics being connected to the non-existing address, the ransomware can detect that it is, in fact, running in a sandbox, and do nothing if so. This is a clever trick used by attackers to mislead sandbox mechanisms.
Cyber-attack and Ransom Collecting
On 12th May 2017 WannaCry began affecting computers worldwide, it is assumed that the initial infection in Asia happened at 7:44 am UTC via the exposed vulnerable SMB port. When executed, the malware first checks for the above-mentioned kill switch domain name. If it is not found, then it starts encrypting the computer’s data. It is basically replacing the existing files with their AES (Advanced Encryption Standard) and RSA (Rivest-Shamir-Adleman) encrypted versions. Thereafter, it attempts to not only to affect computers on the same network but also to exploit the SMB vulnerability to spread out to random computers on the Internet. The payload of the ransomware changes the desktop wallpaper and displays a message informing the user that files have been encrypted and demands a payment of around $300 in Bitcoin within 3 days, or $600 within seven days. To collect the ransom, 3 hard-coded Bitcoin wallets (addresses) were used. According to Wikipedia article about WannaCry; as of 14th June 2017, at 00:18 ET, a total of 327 payments totaling $130,634.77 or 51.62 XBT had been transferred. (XBT: Bitcoin currency. 1 XBT is worth approximately $2500)
Responses from Experts After finding out and turning the kill switch on, it severely slowed the spread of the initial infection and bought some time that was well used to deploy the required defensive mechanisms throughout the world. Researchers discovered that Windows encryption APIs used by the WannaCry may not completely clear the prime numbers used to generate the payload private keys, from the PC’s memory. It eventually paved the path to retrieve the required key if they had not been overwritten or cleared from the residing memory location. WannaKey is an automated tool developed by a French researcher which make use of the above behavior to find out the private key on a Windows XP system. Later, after releasing the patch for the Windows XP versions and for Windows Server 2003, the head of Microsoft Cyber Defense Operations Center, Adrienne Hall, said that “Due to the elevated risk of destructive cyber-attacks at this time, we made the decision to take this action because applying these updates provides further protection against potential attacks with characteristics similar to WannaCrypt”. Moreover, experts advise against paying the ransom due to zero reports of people getting their data back even after paying the ransom. Also, the high revenues and higher publicity could also have encouraged new types of campaigns like the recent Petya attack, which is a cyber-attack began in Ukraine on June 27 and spread to affect many of the world’s largest companies. Upon infection, it encrypts its victims’ computer files and demands a ransom payment to unscramble them – but is in fact purely of a destructive nature. Even though Petya was made to look like a ransomware, expert’s idea is that it is not. Experts suspect that the motive behind the Petya attack was to target Ukrainian organizations, and was made by the criminal masterminds of Russia (or some suspects the Russian government).
Impact of WannaCry
This ransomware attack was unprecedented in scale according to Europol. According to Kaspersky Lab, the four most affected countries were Russia, Ukraine, India, and Taiwan. It also affected many NHS (National Health Service – UK) hospitals in England and Scotland, and up to 70000 devices including, MRI scanners, blood-storage refrigerators, and theatre equipment – may have been affected. ‘Nissan Motor Manufacturing UK’ in Tyne and Wear, England, halted production at several sites in an attempt to stop the spread of the ransomware. It was estimated that the losses due to WannaCry might be within the ballpark of hundreds of millions.
Latest trends
Later, hackers have fixed the Achilles’ heel of the ransomware and the updated version doesn’t contain a kill switch. Organizations have been urged to update their systems immediately to ensure that they are not affected by the ransomware. Furthermore, any systems affected by the WannaCry will have DoublePulsar; a backdoor tool, which is also released by the Shadow Brokers. WannaCry code can take advantage of any existing DoublePulsar infection, or installs it itself. Therefore, DoublePulsar will need to be removed by using an anti-malware or anti-virus software. Also, it is possible to disable the SMBI file protocol, which the worm within the malware was used to spread across the networks.
It is apparent that the trends in ransomware business are ever evolving. That is why it is always a good idea to protect yourself against data loss with regular backups and frequent security updates.
Sources:
https://www.cnet.com/news/wannacry-ransomware-patched-updated-virus-kill-switch/
http://www.wired.co.uk/article/wannacry-ransomware-virus-patch
https://blog.malwarebytes.com/threat-analysis/2017/05/the-worm-that-spreads-wanacrypt0r/
Thanks 😃